這章觀察另一種PowerShell連入的事件的日誌
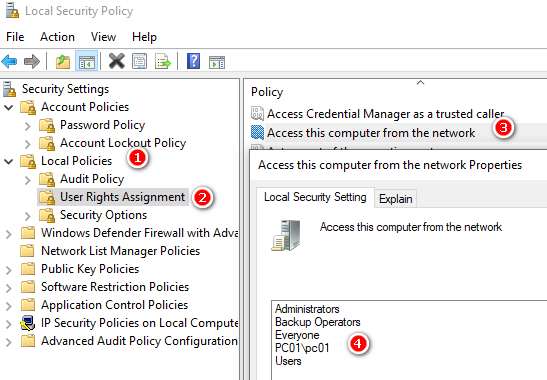
嘗試連線失敗,EventLog Security 4703 Token Right Adjusted Events
──(root㉿kali)-[/home/kali]
└─# pwsh
PS /home/kali> Enter-PSSession 192.168.190.129 -Credential pc01 -Authentication Negotiate
PowerShell credential request
Enter your credentials.
Password for user pc01: ************
Enter-PSSession: Connecting to remote server 192.168.190.129 failed with the following error message : MI_RESULT_FAILED For more information, see the about_Remote_Troubleshooting Help topic.
Start-Service WinRm
Enable-PSRemoting –force
PS C:\Users\pc01> Get-NetConnectionProfile
Name : Unidentified network
InterfaceAlias : Ethernet1
InterfaceIndex : 2
NetworkCategory : Public
IPv4Connectivity : LocalNetwork
IPv6Connectivity : LocalNetwork
...
PS C:\Users\pc01> Set-NetConnectionProfile -Name "Unidentified network" -NetworkCategory Private
Get-WinEvent -FilterXml '
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">*[System[(EventID=4776 or EventID=4672 or EventID=4624) and TimeCreated[timediff(@SystemTime) <= 3600000]]]</Select>
<Select Path="Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational">*[System[(EventID=261 or EventID=1149) and TimeCreated[timediff(@SystemTime) <= 3600000]]]</Select>
</Query>
</QueryList>
' |
Select-Object Id, TimeCreated,
@{Name="LogonType"; Expression={$_.Properties[8].Value}},
@{Name="AdditionalInfo"; Expression={$_.Properties[10].Value}}
從EventLog看起來,處在連線狀態就會一直有4624 LogonType 3 的事件產生
Id TimeCreated LogonType AdditionalInfo
-- ----------- --------- --------------
4624 9/22/2024 6:51:25 AM 3 NTLM
4776 9/22/2024 6:51:25 AM
4624 9/22/2024 6:51:25 AM 3 NTLM
4776 9/22/2024 6:51:25 AM
4624 9/22/2024 6:51:24 AM 3 NTLM
4776 9/22/2024 6:51:24 AM
4624 9/22/2024 6:51:24 AM 3 NTLM
4776 9/22/2024 6:51:24 AM
4624 9/22/2024 6:51:24 AM 3 NTLM
4776 9/22/2024 6:51:24 AM
4624 9/22/2024 6:51:23 AM 3 NTLM
4776 9/22/2024 6:51:23 AM
4624 9/22/2024 6:51:23 AM 3 NTLM
4776 9/22/2024 6:51:23 AM
4624 9/22/2024 6:51:23 AM 3 NTLM
4776 9/22/2024 6:51:23 AM
4624 9/22/2024 6:51:22 AM 3 NTLM
4776 9/22/2024 6:51:22 AM
4624 9/22/2024 6:51:22 AM 3 NTLM
4776 9/22/2024 6:51:22 AM
4624 9/22/2024 6:51:22 AM 3 NTLM
4776 9/22/2024 6:51:22 AM
4624 9/22/2024 6:51:21 AM 3 NTLM
4776 9/22/2024 6:51:21 AM
4624 9/22/2024 6:51:21 AM 3 NTLM
4776 9/22/2024 6:51:21 AM
4624 9/22/2024 6:51:20 AM 3 NTLM
4776 9/22/2024 6:51:20 AM
在Sysmon日誌中可以觀察到Wsmprovhost embedding 的紀錄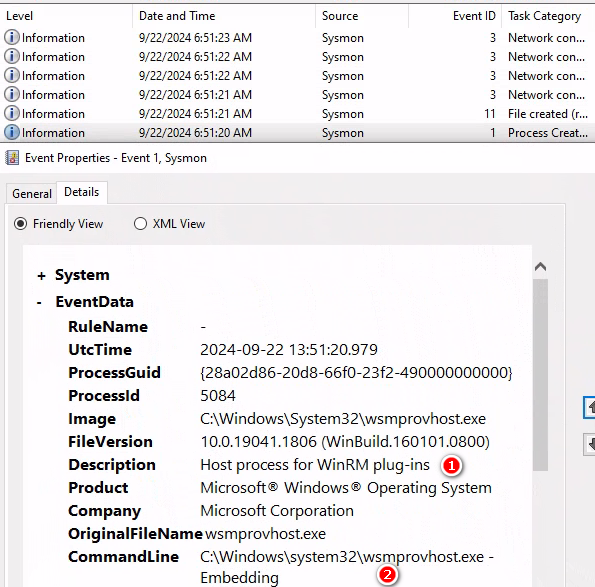
如何執行遠端 PowerShell Script
https://ithelp.ithome.com.tw/articles/10186746
about_Remote_Troubleshooting
https://learn.microsoft.com/zh-tw/powershell/module/microsoft.powershell.core/about/about_remote_troubleshooting?view=powershell-7.4
T1021-006-win-远程powershell会话
https://red.y1ng.org/0xA_%E6%A8%AA%E5%90%91%E7%A7%BB%E5%8A%A8/T1021-006-win-%E8%BF%9C%E7%A8%8Bpowershell%E4%BC%9A%E8%AF%9D/
HOW TO INSTALL AND USE EVIL WINRM IN KALI LINUX
https://medium.com/@josicaleksandar981/how-to-install-and-use-evil-winrm-in-kali-linux-db7b73280ac3
